Increase of DDoS attacks Q1 2019
“In comparison of Q4 2018, Serverius had a increase of DDoS attacks of 430% in Q1 2019. The average DDoS attack changed was also way more professional than the same period last year. The war of PPS has started.”
Although Q4 2018 was fairly quiet, the year 2018 set a new records at the amount of DDoS attacks on client Serverius protects. But during the first quarter of 2019 our support department saw a huge increase of DDoS attacks, way more volume and sophisticated DDoS attack techniques than in the same period last year.
May 2, 2019At my daily work as Serverius support engineer I monitor many DDoS attacks which range from pair Gigabits per second to hundreds. Most of them are mitigated automatically, some will need to have some adjustments on their protection layer to work a bit better but in general I’m quite proud of result of our systems an our support team.
During the day I see all kinds of automated volume layer 3/4 botnets, manual controlled layer 7 attacks incoming from all route directions from the internet. Nothing new like before, but currently we see more and more attacks with a short duration with a high number of packets. Attackers know that with a few hundred Gbps of traffic it’s hard to fill up all uplinks these days and these volume attacks are quite simple to mitigate by cloud scrubbing parties like us. So they try to add some extra souse to it: extra Packet Per Second (PPS). The reason for this is that they know that the more PPS a scrubbing provider will receive, the more resources like CPU and memory it will need to process, and the more network hardware and other resources are needed to mitigate them. Based on what I hear from new clients, most smaller DDoS scrubbing providers currently have problems with this. Glad fully our capacity is able to hold it all, it never reach the more than 25% of the total capacity.
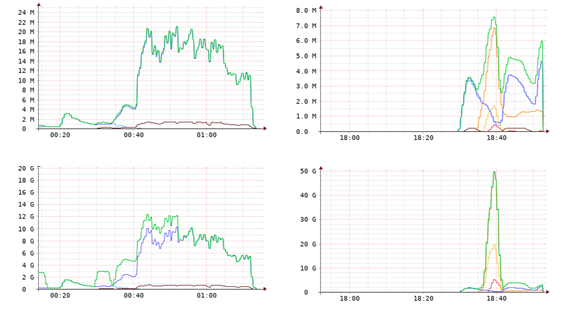
On the left side of the image above you see some samples of DDoS attacks we mitigated this week. Like you can see, the ratio of the number of packets (MPkts= million packets per second) to the attack bandwidth (Gbps=Giga Bits per second) is always likely to be 10 per cent. Thus 10 Gbits/s= 1 M Pkts/s. Whereas on the right side, you see a big contrast in ratio, 1 Gbits/s= 2 M Pkts/s, thus 200 %. This huge different has to do with the nature of the attack. On the left side the most attacks were DNS UDP amplification where you see high bandwidth and low amount of packets while the right side contains samples of TCP flood (SYN, SYN-ACK, FIN,..etc) where you see less traffic and more packets.
Exhaust by CPU & RAM resources
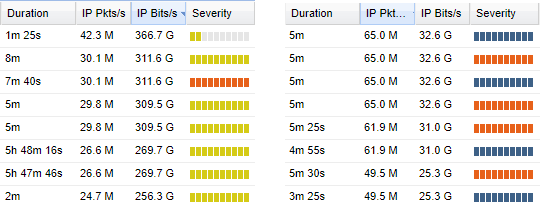
Another nice DDoS sample of the difference between a normal volume attack and some TCP SYN flood where the amount of PPS is way much more. Each appears to have different attacks techniques and will need totally different protection mechanisms to stop the bad traffic.
The first one tries to exhaust the target IP its resources (RAM/CPU) by overwhelming it with fake requests and prevent some of- or all the legitimate requests from being fulfilled. Examples of this kind of attacks are SYN floods, fragmented packet attacks, Ping of Death, Smurf DDoS and more. In this case, the attack consumes actual server resources, or those of intermediate communication equipment, such as firewalls and loadbalancers. They are measured in PPS because they don’t target the uplink bandwidth of the victim. However, it is not easy to generate effective attacks because they need huge resources to be performed and the only successful way to generate them is using wide Botnet.
The second one is to send a larger amount of traffic to the target, trying to use up all its uplinks bandwidth causing congested uplinks and preventing the legitimate traffic from being delivered to the target. For instance, to get down a server with 10 Gbps uplink, all you need to do is to download a script to perform a DNS amplification attack and run it on a normal server with 1 Gbps uplink. The script sends out a DNS query with the IP address of the target to an open DNS resolver, prompting it to reply to that address with a DNS response. With numerous fake queries being sent out, and with several DNS resolvers replying simultaneously, the victim’s network can easily be overwhelmed by the sheer number of the DNS responses. The script can inflate these UDP packets’ size, making the attack as potent as to bring down even the most robust network infrastructure.
The CPU and bandwidth innovation race of the internet makes it relatively easy to generate a huge number of dirty packets and bandwidth to the target. And it has contributed significantly to increasing hackers’ capabilities. In addition, DDoS dark market has also reduced the barriers to criminals to carrying out these attacks in terms of technical capability and cost because like it was in the past and also probably will stay in the future, everyone still can hire a simple DDoS for less than a 100,-.
High availability
Although the worldwide cloud DDoS scrubbing industry wants to make everyone believe, it’s not always possible to separate all dirty data traffic from the clean. Because when filters are set to strict, false positives will arise. Therefore its better to leave some dirty traffic threw the DDoS protection mechanisms. In general 1%, still reaching is the target application, so its hosted solution should be able to handle this without going offline.
When a server crashes because it receives less then a hundred Mbps of DDoS traffic, the blame lies with the server itself. For example, sometime we receive a complain from a new client that our protection system passed DDoS traffic and their server was crushed. When I checked our monitoring systems, I saw that a 400Gbps UDP with a 20Gbps TCP SYN attack was mitigated very well but it passed some dirty traffic of only 20Mbps… So it is wrong to believe that all DDoS traffic can always be completely blocked, at least as of this writing. In other words, a good server (farm) should be able to handle a small amount of DDoS traffic even if it is under protection.
So there is no exception? yes there is! When our protection cloud is used to protect web applications a Web Application Firewall can be used under the DDoS protection. This proxy based service will receive all dirty traffic which is left and will only forward normal requests. And even if a botnet is using normal requests, a captcha will block any bot behind it. Because of our Qbine platform is fully custom build, written with the programming language GO which is running in a multi-site Kubernetes cluster, we are able to handle millions of requests per second. More about the new Qbine platform my colleague will blog next month.
Sophisticated attacks
As attacks have become more sophisticated, they have become a greater concern to IT executives surveyed by NISC. NISC includes over 170 senior security experts, primarily C-Suite executives and senior decision makers, representing both small and large companies. In the most recent survey of these professionals, most indicated that they believe that DDoS is the top threat to their network. Forty eight percent of executives surveyed believe that DDoS attack threats have increased, while 42% believe that they had increased their ability to respond to such threats. Our statistics support the result of this survey. In fact, we witness every day the birth of new technical capabilities and who knows what tomorrow would bring…
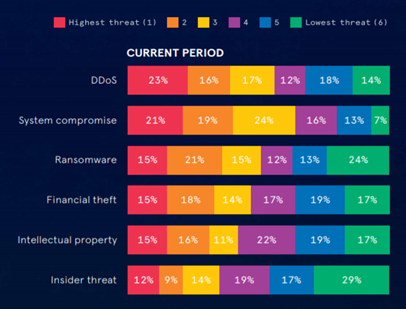
Cyber threats ranked in order of concern, January 2019 NISC report
Governments are aware of the DDoS threat and start to enforce laws, like Incident response policy, to collect statistics on which they can rely to have a better insight and take the suitable measures against it. Besides, governments start to force sensitive organizations like banks to have mitigation services by reliable security companies. Your organization should be prepared as well, and prevention is better than cure because once a DDoS attack is underway and your server is offline, getting it back to normal can be costly. Website downtime can impact both your business sales and your reputation. Thus, make sure your business is safe at any time.